Securing Server Infrastructure: Mitigating Information Disclosure Risks
Written on
Chapter 1: Understanding Server Information Disclosure
In the current digital environment, where cyber threats and data breaches are on the rise, protecting your server infrastructure is essential. A significant security issue organizations face is the risk of “Server Information Disclosure.” This occurs when critical details about a server's setup, technology stack, or internal workings are unintentionally revealed to unauthorized individuals. Such vulnerabilities can be exploited by hackers to identify weaknesses and mount targeted attacks, potentially resulting in data theft, service interruptions, and harm to the organization's reputation.
Section 1.1: The Role of Istio Service Mesh
A common example of information exposure is the Server HTTP Header, which is typically found in most HTTP responses. This header may reveal server details that vary with the technology stack, such as Jetty or Tomcat. However, if you utilize a Service Mesh like Istio, the header might display a value like istio-envoy, as illustrated below:
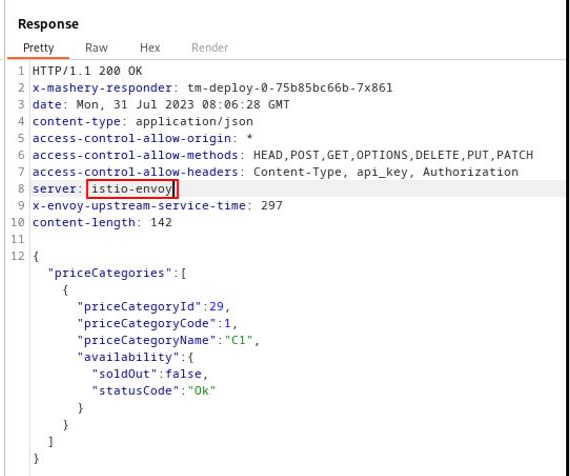
The significance of protecting against information disclosure extends across various security dimensions:
- Data Privacy: Leaking server information can compromise confidential data, eroding user trust and breaching regulations like GDPR and HIPAA.
- Minimized Attack Surface: Concealing server specifics reduces the potential points of attack available to intruders.
- Security by Obscurity: Though not entirely foolproof, limiting the information available can create an additional barrier for hackers attempting to gather intelligence.
Subsection 1.1.1: Mitigation Strategies with Istio
To address these vulnerabilities using Istio, you can establish rules to manipulate HTTP headers according to your requirements. The official documentation provides guidance on how to do this, including the removal of unnecessary headers. Below is a sample configuration for your VirtualService:
apiVersion: networking.istio.io/v1alpha3
kind: VirtualService
metadata:
name: k8snode-virtual-service
spec:
hosts:
- "example.com"
gateways:
- k8snode-gateway
http:
headers:
response:
remove:
- "x-my-fault-source"
route:
destination:
host: k8snode-service
subset: version-1
Unfortunately, this method does not apply to all HTTP headers, particularly the standard ones defined by the W3C, like the Server HTTP header. To manage these, you’ll need to utilize an EnvoyFilter, which is a powerful feature within the Istio Service Mesh. According to Istio’s official documentation, an EnvoyFilter allows you to tailor the Envoy configuration created by Istio Pilot, enabling you to change specific fields, insert custom filters, or even establish entirely new listeners and clusters.
Section 1.2: Implementing EnvoyFilter to Remove Headers
Having established the need for a custom EnvoyFilter, let’s review the specific configuration required to eliminate the Server header. Below is an example of such an EnvoyFilter:
apiVersion: networking.istio.io/v1alpha3
kind: EnvoyFilter
metadata:
name: gateway-response-remove-headers
namespace: istio-system
spec:
workloadSelector:
labels:
istio: ingressgatewayconfigPatches:
applyTo: NETWORK_FILTER
match:
context: GATEWAY
listener:
filterChain:
filter:
name: "envoy.filters.network.http_connection_manager"
patch:
operation: MERGE
value:
typed_config:
"@type": "type.googleapis.com/envoy.extensions.filters.network.http_connection_manager.v3.HttpConnectionManager"
server_header_transformation: PASS_THROUGH
applyTo: ROUTE_CONFIGURATION
match:
context: GATEWAY
patch:
operation: MERGE
value:
response_headers_to_remove:
- "server"
In this configuration, you specify the workloadSelector to indicate where the EnvoyFilter will be applied, specifically to the istio ingressgateway. The configPatches section allows for the necessary customizations. Two actions are taken here, both focusing on the GATEWAY context, affecting NETWORK_FILTER and ROUTE_CONFIGURATION. The first patch incorporates the custom filter http_connection_manager to manipulate the HTTP context, including HTTP headers. The second patch removes the Server header, as specified in the response_headers_to_remove option.
Conclusion: Elevating Server Security with Istio
Implementing these configurations can be complex, but they showcase the robust capabilities of a sophisticated service mesh like Istio. This functionality allows for meticulous control over server behavior, which can significantly enhance security for workloads managed within the Service Mesh.
In a constantly changing landscape of cybersecurity threats, protecting your servers from information exposure is vital for safeguarding sensitive data and preserving your organization’s integrity. Istio equips you with the necessary tools for effective traffic management, encryption, and access control.
Remember, proactive measures to address vulnerabilities are crucial for optimal server security. Take the first step in implementing Istio to strengthen your server defenses.