Understanding Various Cybersecurity Teams in Information Security
Written on
Introduction to Cybersecurity Teams
Organizations depend on teamwork to safeguard their assets and maintain security. Multiple teams collaborate to protect the organization, employing both offensive and defensive strategies. Commonly deployed teams include the Red Team, Blue Team, and Purple Team, each specializing in areas such as network security and firewalls.
Understanding the Roles of Cybersecurity Teams
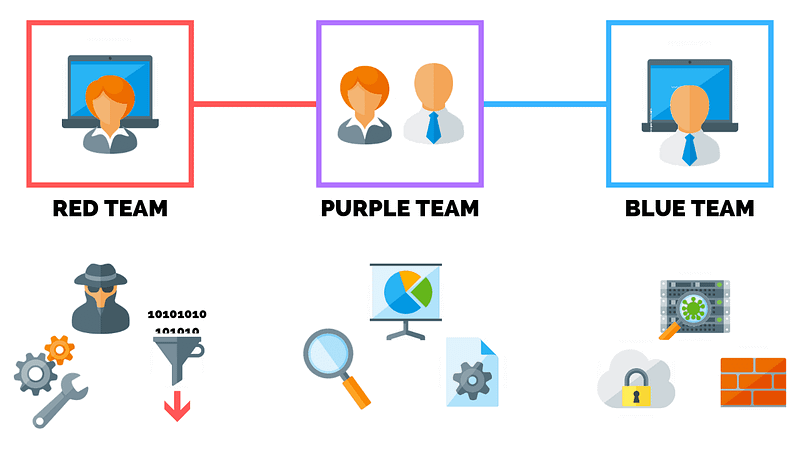
Within the realm of information security, the Red Team is often recognized, but the Blue and Purple Teams also play critical roles in both offensive and defensive assessments. These teams are essential for securing the organization against potential threats. They implement various defensive measures, including the establishment of firewalls, cyber security protocols, and bug bounty programs.
Red Team Responsibilities

The Red Team adopts an offensive strategy to evaluate the organization's defenses. They simulate hacker behavior to identify vulnerabilities by testing the organization's systems and exploiting weaknesses. When new features are developed, Red Team members are tasked with searching for bugs, probing for vulnerabilities such as privilege escalation and SQL injection (SQLi).
The primary aim of the Red Team is to uncover vulnerabilities, challenge assumptions, and explore various attack vectors. They assess the organization's security stance to predict how well it might withstand real-world attacks before they occur. These exercises are often termed "red-teaming" due to the simulated attack scenarios they conduct.
Blue Team Functions
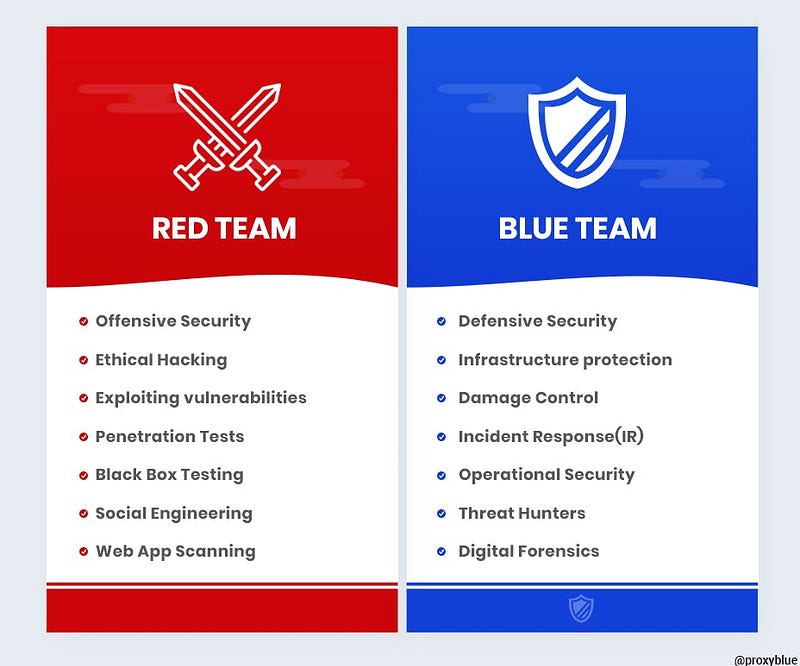
The Blue Team serves as defenders, tasked with shielding the organization from external threats such as cyberattacks. Their responsibilities include developing and implementing defensive measures tailored to the unique threats faced by the organization, which vary based on technology and infrastructure.
A proficient Blue Team analyzes past attack reports, network traffic, and user behavior to create effective preventive strategies. These strategies may involve the use of Intrusion Prevention Systems (IPS) and Intrusion Detection Systems (IDS). By training personnel on response protocols, the Blue Team enhances the organization’s resilience against similar future threats.
To effectively monitor threats, Blue Teams leverage a variety of tools, including Security Information and Event Management (SIEM) systems. They customize rule sets based on identified threats and vulnerabilities, allowing for real-time alerts when potential dangers arise.
Purple Team Collaboration
The Purple Team acts as a bridge between the Red and Blue Teams, facilitating collaboration. Their primary focus is to enhance the organization's overall security posture through continuous feedback and shared knowledge. This collaboration leads to improved security measures without additional financial burden.
Organizations may engage in one-time or ongoing Purple Team operations, where security objectives, timelines, and deliverables are clearly defined. These scenarios allow for structured evaluations of the organization’s security posture and employee awareness.
Conclusion
We have explored the distinct roles of various cybersecurity teams, emphasizing their importance in bolstering organizational security. Effective communication and knowledge sharing among these teams enable organizations to achieve robust security outcomes with minimal resources.
This video explores the different types of cybersecurity teams, including their roles and responsibilities in safeguarding organizations.
In this video, learn about Purple Teaming and the dynamics between Red and Blue Teams, highlighting how they work together to enhance cybersecurity strategies.